2026 Technical Hiring Playbook: How to Spot the Fakes Without Losing the Best Talent
By
Samantha Cox
•
Dec 15, 2025
If a resume looks too good to be true in 2026, maybe it is. We are currently living through a scary reality in tech hiring. After verifying hundreds of engineers, Fonzi data reveals a startling statistic: roughly 10% of applicants are fraudulent. These go beyond exaggerations; they are often completely fabricated or stolen identities, likely state sponsored actors (e.g., North Korean actors).
The scammers have reverse-engineered the hiring process. They know exactly what hiring managers want to see. As a result, we have reached a tipping point where "too polished" is actually suspicious, and the engineer with the awkward photo and a typo is likely the legitimate talent you need.
The Fraud Behavior: How Scammers Game the System
Fraud has metastasized from simple resume embellishment to sophisticated, AI-driven identity theft. However, there is no single "magic bullet" for detection. Isolated signals, like a typo or a strange location, can easily belong to a genuine engineer who simply isn't good at self-promotion. The secret to identifying fraudulent applicants lies in pattern recognition: catching a cluster of flags rather than a single mistake. Fonzi employs layered AI workflows to surface these inconsistencies at scale, flagging profiles for human review only when the data points stop adding up. Below are the specific strategies sophisticated actors are using right now.
1. The Identity Thieves (The "Perfect" Ghost)
These applicants steal real identities to bypass initial screens. They find a real engineer’s LinkedIn, copy the background, and present it as their own.
The "Remote Only" Trap: These applicants are almost always "remote only" and are state sponsored actors or sophisticated criminal organizations.
The Email Signal: A major tell is the email address. While the name matches the resume, the email often contains an excessive number of random digits (e.g.,
name.surname.123@gmail.com).The "Perfect Area Code" Match: Be skeptical if an area code matches a candidate's current residence exactly. Most professionals retain numbers tied to hometowns or colleges, making a perfect geographic match suspicious.
VOIP Check: A quick lookup can reveal if the number is VOIP-based, a common tool used by identity thieves to mask their true location.
The Location Spoof: They list random cities or small towns to explain why they aren't in a tech hub, or use locations that are suspicious.
2. The AI Slop Merchants (The "Keyword" Stuffers)
These candidates use LLMs to generate resumes that hit every single requirement in your job description.
Impossible Timelines: They list technologies before they were even invented, such as claiming experience with a framework years before its release.
Tech Stack Mismatch: To match job requirements, fraudsters stuff keywords that contradict their alleged employer's actual infrastructure. Watch for specific impossibilities, such as listing GitLab experience at a company like Stripe, or citing technologies that weren't part of that company's stack.
Tech Soup: They stuff overlapping or incorrect technologies into a single role, such as listing both React and Angular for the same project.
Robotic Interviews: When you get them on a call, their responses sound too coherent, like they are reading an AI-generated script off the screen with zero tonal variance.
Example Candidates: The "Perfect" Fake vs. The "Suspicious" Real
To understand why the "perfect" candidate is often the most dangerous one, we analyzed two profiles recently processed by Fonzi. These examples illustrate the "Paradox of Perfect": a backward reality where polished resumes are red flags, and genuine talent looks suspiciously unoptimized. This comparison highlights why there is no magic bullet for detection and exposes the growing challenge for real engineers trying to break through the noise of sophisticated fraud.
Candidate A: The Imposter
The Profile: A Senior Software Engineer with a verified LinkedIn badge, professional profile, and flawless experience at recognizable Tier-1 companies like Cruise. Every bullet point was a polished, high-impact achievement.
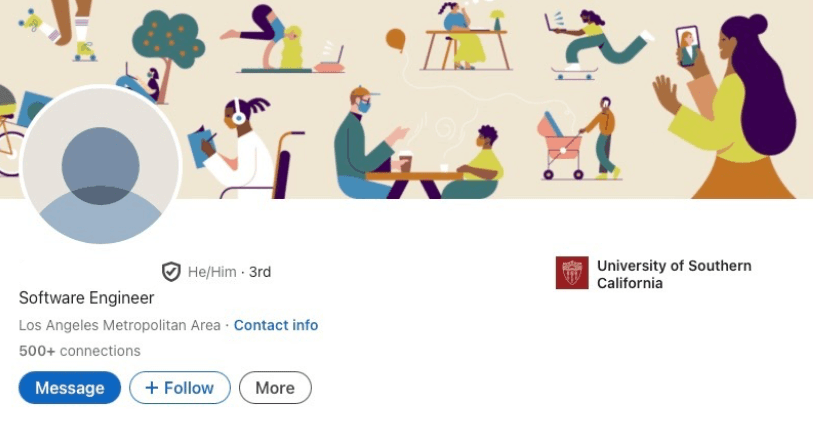
Why Recruiters Loved Him: This profile was algorithm-perfect. It hit every desirable keyword (Golang, PyTorch, React.js) and carried the high-signal trust of a verified badge, making the phone screen invitation feel like a guaranteed win. The profile is so good, it’s easy to drop your guard.
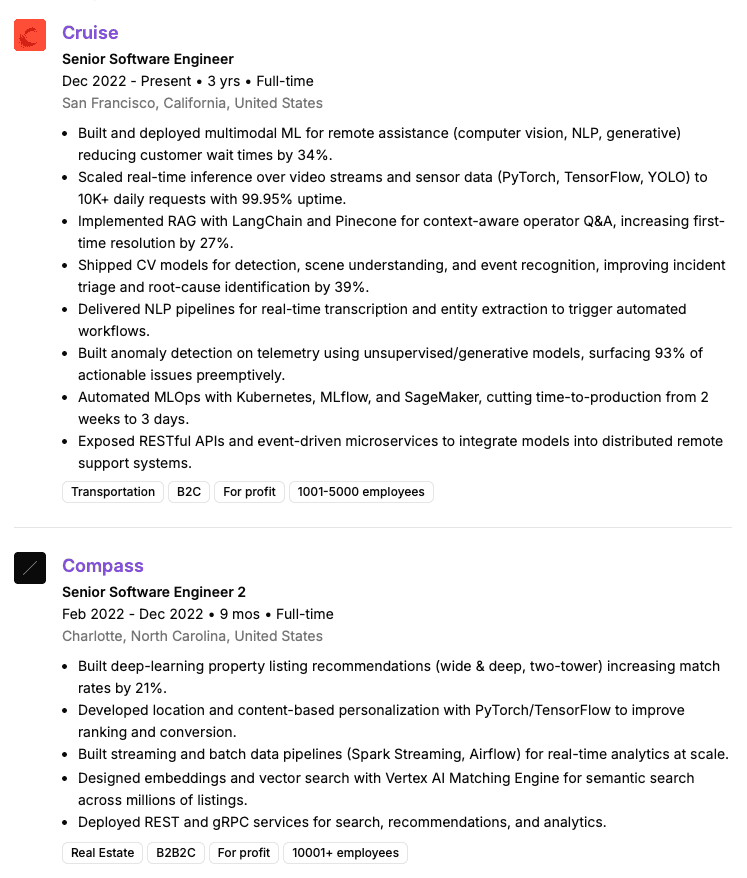
The Verdict: It was a stolen identity.
How Fonzi Caught It:
Here are the tell tail flags that our system automatically recognized preventing this fraudulent applicant from moving forward and hoodwinking our clients.
Background Mismatch: There were mismatches between the candidates resume and LinkedIn.
AI Slop: The resume tripped multiple flags that signal keyword stuffing behavior. An engineer of the real person’s caliber would likely describe themselves in this way.
The Email Signal: The email used to apply was
name.surname.770@gmail.com.VOIP Check: The phone number list is for a Twilio VOIP.
Unfortunately for the real candidate, someone is out there applying to jobs and impersonating them.
Candidate B: The Real Deal
The Profile: Software Engineer at Google with a stiff, passport-style photo, barely 318 connections, a verified profile, and typos in his job description.
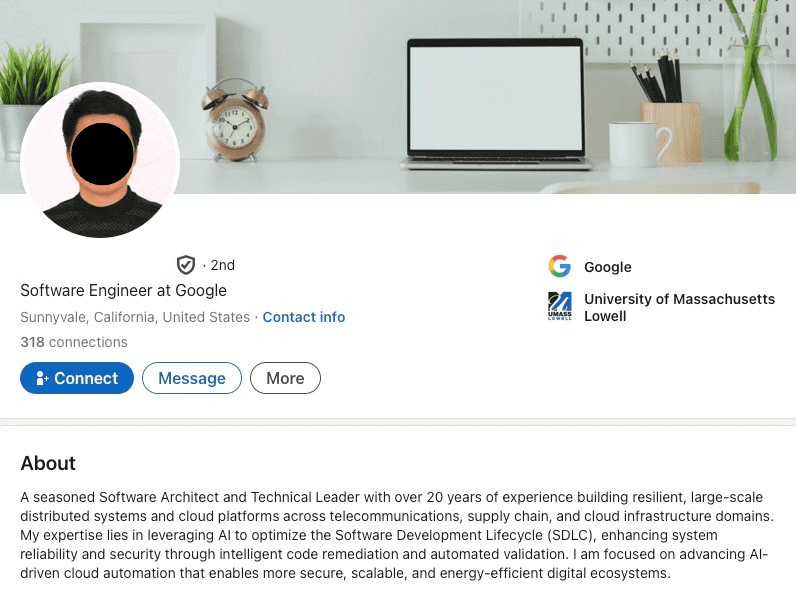
To a human recruiter, this LinkedIn profile triggers multiple red flags typically associated with fraudulent accounts. Despite being verified, the profile exhibits several characteristics that make recruiters suspicious.
The Reality: He is 100% legitimate. He simply hasn't optimized his career history for an algorithm because he has been too busy actually writing code. While the "fake" candidate spent hours polishing their summary, this engineer was busy building systems.
Why Recruiters May Reject Him: To a human recruiter, this LinkedIn profile looks like a textbook impersonator.
The awkward LinkedIn aesthetic between profile and cover photos
Lack of a vast network (under 500 connections) are immediate signals of a farmed or fraudulent account
"Suspicious" offshore visually looking LinkedIn profile
A background from outside the US prior to working at a FAANG company
Typos within his LinkedIn profile
And so on….
How Fonzi Verified Him: All candidates active in Fonzi’s marketplace explain a technical project they did to our AI agent and then complete a phone screen with one of our human concierge recruiters.
Throughout the application process, this candidate raised neither agentic nor human red flags. He is a real person who actually works at Google and simply doesn't view his LinkedIn profile as a priority. He hasn't optimized his career history for the job market because he has been too busy writing code, and when questioned about his work, he can clearly explain in terms of tangible business impact.
The Lesson: In 2026, legitimate senior engineers often have messy, unoptimized digital footprints. Conversely, fraudsters consistently have the most curated ones. This is the very scary reality: the deception tactics will only grow more sophisticated and harder to discern.
Advice for Recruiters: There Is No Magic Bullet
There is no single button to "Stop Fraud." It requires a multi-layered defense strategy combining AI heuristics with human concierge intuition.
1. The "Human" Loop
Video Non-Negotiables: We require video calls, no virtual backgrounds allowed, as these hide potential proctors.
The Context Trap: We ask questions that only a real person would know without context, such as "What was your college mascot?" without naming the school.
2. The AI Forensic Layer
Thinking Models: We utilize the latest flagship models to evaluate work experience for plausibility, flagging "impossible" scopes of work.
Cross-Referencing: We check for "digital ghosts." Real people have networks. If a profile has fewer than 100 connections or has been deleted, it is a high-probability fraud signal.
Physical & Contact Information: We check for suspicious email formats, the use of VOIP phone numbers, and unusual places of residence, among other signals, to ensure people are who they say they are.
Advice for Candidates: Things to Avoid
If you're a real engineer, your goal is no longer to create a "perfect" resume for each job application. You need to focus on specificity and authenticity to avoid being flagged as a fake. Speak to business impact instead of specifically tools and technologies.
Be Specific, Not Flawless: Avoid generalized bullet points generated by AI. If you say you used Kubernetes, be prepared to talk about a specific, complex issue you solved with it. Detail the real-world business impact of your work.
Show Your Network: Real professionals have networks. Ensure your LinkedIn connections are genuine, not just a farmed list of strangers. Human recruiters and future employees may discount you for your online presence.
Embrace the "Messy": Humans are inherently messy. Don't be afraid to show the rough edges. Speak in ways that avoid appearing like LLM-generated content. If using AI, improve bullet point by bullet point vs generating a resume with an LLM.
Content Information: Avoid using VOIP (burner) phone numbers and generic, disposable email accounts. Your contact info should be easily verifiable. Using an old university email (.edu) is a strong signal of authenticity. Make your primary email visible on your LinkedIn profile to eliminate any reason for a recruiter to flag it as suspicious.
Own Your Story: Be ready to answer highly personalized questions in interviews that only you would know (like details about your college or former coworkers). Authenticity is your best defense against fraud detection.
Conclusion
The hiring playbook from three years ago doesn't work anymore. The signals we were trained to trust, polished profiles, clean resumes, and professional presentation, have been gamed by fraudsters.
As we move deeper into 2026, the cost of bad hiring goes beyond a poor culture fit, it includes hours of engineering time spent interviewing people who don't even exist. Real talent might look "suspicious" because they are not optimized for your hiring playbook.
Don't be fooled. Verify the human behind the application.




